Hi, I’m glad I’ve come across this place. I’ve worked in IT for almost 20 years and have experience in a lot of things and not so much in VPNs.
Our church has three buildings that do no touch and are on a downtown city area, and each building has it’s own cable internet access. I’d like to connect the PCs in those buildings with a type of VPN to easily access each of them on the “same” network. The only issue is, I’m not very familiar with VPNs (other than TeamViewer). We’d like the data to be secure and (of course) affordable.
Would anyone have any ideas?
Thank you.
I use pfsense firewalls with an always on ipsec VPN connection. Each building will be on a different subnet, but you can talk across the VPN.
What gateway (i.e. router, firewall) do you have at each location at present? As much as I’m not that fond of Meraki’s licensing strategy (pay full price for the equipment and then pay rent on top of that to keep using it), they do make the VPN thing exceedingly easy. It’s to the point that one organization I helped had managed to get a VPN set up between two offices with Meraki gateways and didn’t even know it!
On the other hand, if your sites all have static IPs, it’s pretty easy to set up VPNs with any commercial grade gateway, and it’s not that bad either if some of the “spokes” off the “hub” have dynamic IPs. It is easier if all sites have gateways of the same brand and operating system.
(On a third hand, do any or all of the buildings have a line of sight path between them? Fixed wireless can work wonders in the right circumstances, if you can see at least one other site from each of the sites.)
There are two ideas:
You say they do not touch. However, if they have line-of-site, you could look at wireless point-to-point Ubiquiti M5’s (we use model NSM5). Here’s a link: https://www.ubnt.com/airmax/nanostationm/ I have this setup at one of our campuses where two buildings are not touching, but needed internet connection to the second. The second building was too small to put in the cost, time, and effort of running fiber… but for about $100 per side, we set this up and it works great!
The second thing is, if they don’t have line-of-site, you could do a site-to-site vpn via the firewall. We have six locations connected together using site-to-site vpn’s. As mentioned above, you’ll need your firewalls to have a static IP from the ISP, and then you can set it up. We use Cisco ASA 5505’s at our Regional Campuses, Cisco ASA 5510 (upgrading to a Cisco ASA 5525-X this year) at our main campus. There is a VPN Wizard from the ASDM (graphical interface), to assist in site-to-site vpn creation, with traffic flowing between campuses. I know others on the form use other firewalls and can speak to those.
Hope this helps!
I use Ubiquiti at my church to connect two buildings that people in times past didn’t think about connecting with conduit. With that said, anyone buying a Ubiquiti bridge today should consider the NanoBeam 5ac line, which can push a couple hundred megabits per second, versus the 60-80mbps that the previous generation NanoStation M5 can realistically do. Those needing up to a gigabit per second should consider the AirFiber 24, as long as the buildings aren’t too far apart (less than, say, 5-7 miles) and the line of sight is perfect. There are plenty of options in the fixed wireless space, but in my opinion Ubiquiti is the best balance of cost with ease of use and reliability (you can spend a lot more to get a little better gear, which may or may not be worth it).
Good call Josh. We put ours in several years ago, glad you were able to recommend newer models! 
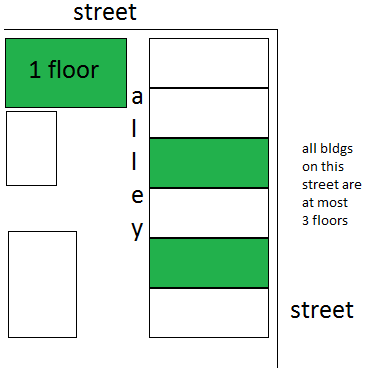
Here’s a layout of the block the buildings are on…
tylerturner
I’ll look into that.
Josh
We just have the standard cable modem/router in each. I don’t have model numbers but can find that out.
Cisco / Josh
One building is a one story and the other two are two story, all on a block with the max distance between being about 150ft. Can the Ubiquiti devices extend internet access from one building to the other two?
You can absolutely extend internet access from one building to the other. When configured properly, Ubiquiti NanoStations or NanoBeams are effectively a layer 2 bridge, so you can extend subnets / VLANs across the link.
One option would be to do two point to point links on different frequencies, with two radios on the upper left building and one each on the buildings on the right side of the map. Alternately, you could put one radio on the upper left building, configured as an AP, and hit it from radios on each of the other two buildings. In this way, your capacity is diminished because both of the other buildings are sharing bandwidth; that may or may not be a problem depending on what performance you need.
On that note, what kind of performance are you looking for, and in terms of communication between the physical spaces, which buildings will be communicating with which other ones at what desired capacity? Knowing that, it’s then possible to get into more specifics.
You could do the following, changing “A, B, C” to different buildings depending which building is considered your “main building”.
If you (Nathan) were going to be well served by VPN connections limited by the upload speeds of the respective cable connections in question, then I think the configuration that Cisco is showing here would suit you very well indeed - and you might even be able to consider dropping down to one internet connection instead of three, if one would be enough to handle the capacity required by the total number of users in all three buildings. This is the best case for wireless links that you’ll find, with all three buildings being not only within line of sight to each other, but also super close, so there will be few other sources of RF interference between your sites. I think this would work excellently for you if you choose to go this route.
Awesome! I think that would be great to be able to extend it with the Ubiquiti devices. I will look into the devices and get a gameplan together. Then present it to our leadership. Again, thank you all very much!