Our top guys keep getting spoofed. I found this article/rule and thought I’d forward it on: https://blogs.technet.microsoft.com/eopfieldnotes/2018/02/09/combating-display-name-spoofing/
Yeah - this will help, but my first question is do you have your SPF, DKIM and DMARC all set up?
Although they don’t really guarantee Spoofing won’t happen, they do tackle the bulk of it.
After that Transport rules like this and few other will really help.
Yes. Unfortunately, those rules are no help against an account set up on gmail with a real person’s name.
I wish I could just block gmail accounts. They do nothing to stem the flow of this stuff — don’t even give you a way to report it.
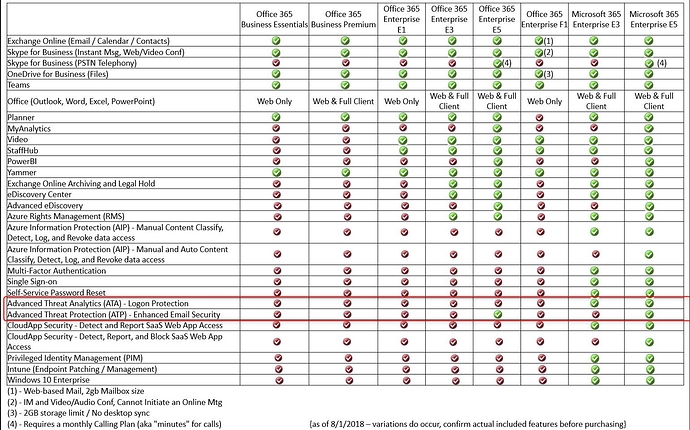
Did you guys purchase licenses for Microsoft ATP? We purchased licenses for around $.60 cents more a month per user and it does this for you.
I saw a price of $.80 yesterday when looking. I’m going to talk to our Microsoft partner. In the meantime, this rule has already stopped a bunch of garbage.
That’s wonderful. Thanks for sharing the link to the rule.
This may help with Gmail: https://support.google.com/a/answer/7577854?hl=en
|Spoofing and authentication settings|Actions|
|Protect against domain spoofing based on similar domain names
Protect against incoming messages from domains that appear visually similar to your company’s domains or domain aliases.
|Protect against spoofing of employee names
Protect against messages where the sender’s name is a name in your G Suite directory, but the email isn’t from your company domain or domain aliases.
|Protect against inbound emails spoofing your domain
Protect against potential Business Email Compromise (BEC) messages not authenticated (with SPF or DKIM), pretending to be from your domain.|*
|Protect against any unauthenticated emails
Protect against any message not authenticated (with SPF or DKIM) by any domain.
|Protect Groups from inbound emails spoofing your domain (beta)
Protect your Google Groups from inbound emails spoofing your domain. You can apply this setting to all groups or to private groups only.|
We get this a lot too. Randomly created gmail accounts using display names of our users. O365 support helped me with a similar rule and used a script to import all our user’s display names to say if it matches an internal user’s display name then prepend a warning message. I’ve decided recently just to prepend the message to ALL outside emails coming in. I’ve noticed some companies doing it lately as well. Do I like doing it? Of course not. However, after multiple emails, training (KnowBe4), etc., we’ve still had users fooled by these emails.
Eric, any way you can share the settings of that rule? Would love to add it to ours.
I’ll message you directly
Also if you’re using Office365 you can go here: https://protection.office.com/antiphishing and click the default policy button to set up another layer of anti-spoofing protection and more 
This is how we have ours set up currently:
How did you get to all those settings. I do not show any policies at that location. If I click the Default Policy button, there are very few settings to choose from.
hm you may have to go through the default policy wizard thing to get it to populate everything. You may need the Enterprise Mobility & Security E3 license and / or Advanced Threat Protection license - do you have those?